The Industrial Unified Namespace (UNS) plays a central role in Industry 4.0, bridging IT and OT systems into a unified data architecture. But securing such a critical infrastructure – as any other – requires careful planning. This article highlights typical security risks of an IT/OT data infrastructure and shows best practices for implementing secure Unified Namespace (UNS) architectures.
OT/IT Security in Industry 4.0
The convergence of Operational Technology (OT) and Information Technology (IT) is a driving force behind Industry 4.0. Production facilities, machines, and control systems are increasingly connected with IT systems, cloud platforms, and data analytics to boost efficiency, transparency, and flexibility. Yet this integration also expands the attack surface: while traditional IT security strategies focus on office and business systems, OT environments require dedicated protection. A successful attack can compromise not only data but also disrupt physical processes — with severe implications for safety, production, and supply chains. To safeguard modern Industry 4.0 architectures, a comprehensive OT/IT security strategy is essential.
Typical Security Risks in OT/IT
The integration of IT and OT systems introduces a range of security risks. Common issues include insecure OT protocols, missing authentication and access control, unpatched systems, insufficient network segmentation, and remote access through open ports. Such vulnerabilities enable attackers to move laterally between IT and OT environments or disrupt critical production processes.
Security Risks in the Unified Namespace (UNS)
| Risk | Typical impact in OT environments |
|---|---|
| Open inbound ports in OT networks | Direct attack surface from outside, bypassing segmentation and firewalls |
| Missing or inadequate network segmentation | Lateral movement of attackers between IT and OT, rapid spread of incidents |
| Too many uncontrolled outbound ports | Exfiltration of sensitive production data, command & control communication |
| Weak or standard authentication (e.g. “admin/admin”) | Unauthorized access, rapid compromise of critical systems |
| Over-privileged collective accounts (lack of least privilege) | Abuse and misuse with a broad impact, actions difficult to trace |
| Unencrypted OT protocols (e.g. Modbus, older S7 versions) | Interception of plain text data, manipulation of communication |
| Decentralized user and role administration | Inconsistent policies, configuration errors, increased attack surface |
| Lack of central monitoring and logging | Late detection of attacks and misconfigurations, difficult forensics |
| Unpatched systems and lack of update strategies | Exploitation of known vulnerabilities, repeated compromises |
| Unpatched legacy systems (end-of-support OS/firmware) | Permanent vulnerability, lack of security fixes, compatibility constraints |
| Insecure default configurations (passwords, open services) | Rapid compromise after commissioning, escalation through chain effects |
Typical Measures for Securing OT/IT Environments
To mitigate these risks, organizations should apply the following measures:
- Eliminate open inbound ports: Inbound ports in OT networks are highly critical as they expose a direct attack surface. Protocols such as OPC UA client-server require inbound ports to write data to OT systems. In contrast, outbound-oriented protocols such as MQTT only initiate connections from OT systems to the broker, eliminating the need for open inbound ports in critical networks. Outbound ports should also be restricted to the bare minimum to ensure controlled data flows.
- Encrypt communication (e.g., TLS, MQTTS): Many legacy OT protocols, such as Modbus or older S7 versions, transmit data unencrypted in plain text. This allows attackers to read sensitive information and manipulate commands, such as changing production setpoints. Converting these protocols into encrypted MQTTS ensures both data confidentiality and integrity.
- Centralize governance: In many OT environments, users, roles, and monitoring are managed separately on individual gateways. This results in inconsistent policies, higher administrative overhead, and security gaps. Centralized governance with consistent role management (e.g., via Microsoft Entra), regular updates and patching, as well as integrated monitoring, backup, and recovery, significantly reduces these risks.
- Implement strong authentication and role-based access control (RBAC): Each user and device should be limited to the minimum rights required (least privilege principle). Weak defaults such as “admin/admin” or over-privileged shared accounts often cause unplanned downtimes due to unauthorized or accidental changes in production. Enforcing centralized and consistent access control minimizes these risks considerably.
Best Practices for Secure Unified Namespace (UNS) Architectures
To build a secure Unified Namespace (UNS) architecture, organizations should implement proven best practices and consistently apply them across the entire UNS environment.
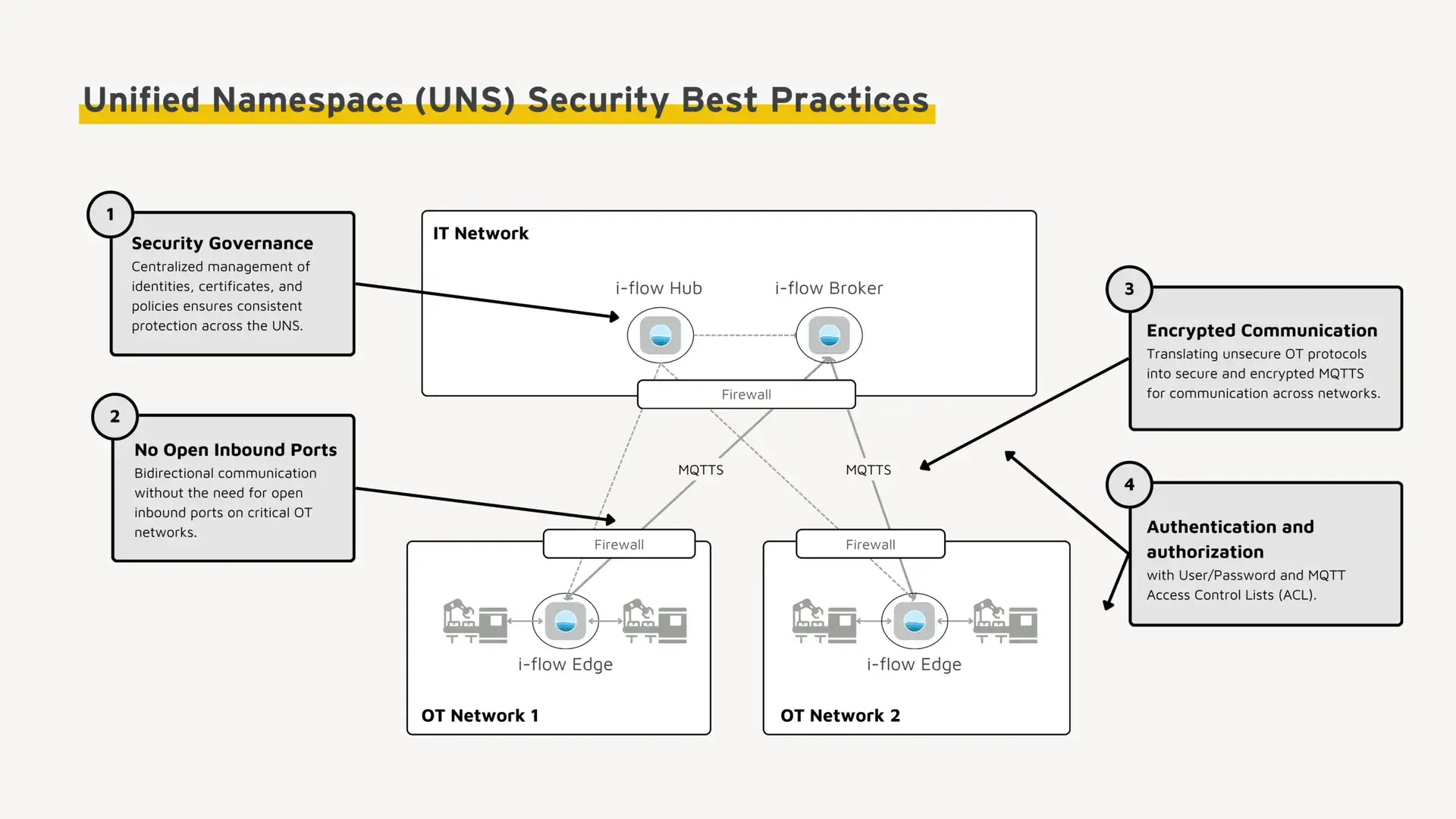
1. Central Security Governance
Centralized security governance significantly reduces risks. Security policies, certificates, roles, and updates are managed uniformly, ensuring that the entire UNS remains consistently protected across sites and regions. Complementary measures such as monitoring, logging, backup, and recovery provide transparency and enable rapid response to anomalies or failures.
Example i-flow UNS:
- i-flow Hub: Central point for configuration, governance and deployment.
- Role and rights management: Defined centrally in the Hub and automatically distributed to Edge and Broker.
- Monitoring & auditing: Unified overview of logs, access events, and system health.
- Automated deployments & updates: Standardized rollouts keep all components secure and up to date.
2. Bidirectional Communication Without Open Inbound Ports
Protecting critical OT systems requires strict network segmentation and firewalls. A distributed UNS architecture supports this segmentation by design, enabling secure and efficient data communication between isolated OT networks and central IT systems — without exposing inbound ports.
Example i-flow UNS:
- i-flow Edge: Converts insecure OT protocols into encrypted, outbound-oriented protocols such as MQTT. Connections are always initiated from inside the OT network, eliminating the need for inbound ports.
- i-flow Broker: Bridges OT and IT with MQTT’s publish/subscribe model, enabling secure data exchange without compromising network security.
3. Converting Insecure OT Protocols to Secure MQTTS
Legacy OT protocols such as Modbus or older S7 variants transmit data unencrypted, making them vulnerable to interception and manipulation. Converting these streams to MQTTS (MQTT over TLS) mitigates these risks: data is encrypted locally in the OT network before being published to the UNS. TLS encryption guarantees confidentiality and integrity end-to-end.
Example i-flow UNS:
- i-flow Edge: Reads data from insecure OT protocols and converts it into encrypted MQTTS within the OT network.
- i-flow Broker: Accepts only MQTTS connections, ensuring that all UNS data flows are encrypted.
- X.509 certificates: Provide mutual authentication between Edge, Broker, and clients, managed centrally in the i-flow Hub.
4. Authentication and Access Control in the UNS
Strong authentication and granular access control are essential for UNS security. Only authorized users and devices should access data and systems, enforced reliably across distributed environments. Following the least privilege principle, each account and device is granted only the rights necessary for its function.
Example i-flow UNS:
- Access control via ACLs: Define client permissions within the MQTT namespace. How it works:
- Client identification through login credentials.
- ACL validation against configured rules.
- Access allowed or denied for publish/subscribe actions.
- Continuous session monitoring to prevent unauthorized activity.
- Username and password protection: Credentials are validated against a central authentication system, with results communicated via standardized MQTT return codes.
- Integration with corporate identity providers: Connection to existing IAM systems (e.g., Microsoft Entra) enables centralized user management and consistent enforcement across the UNS.
Unified Namespace (UNS) Security Checklist
The following checklist summarizes the most important best practices for a secure Unified Namespace (UNS) architecture. It serves as a practical guide to avoid typical vulnerabilities.
| Category | Checkpoint | Why it is important | Evidence / implementation |
|---|---|---|---|
| Centralized security governance | Centralized management of policies, roles and certificates | Consistent security across locations; avoids configuration drift | Proof of central platform (e.g. hub); documented policies & role concepts |
| Monitoring & auditing established | Early detection of anomalies and misconfigurations | Central log overview; defined alarm rules; regular audit reports | |
| Backup & recovery defined and tested | Secure recovery in the event of failures or attacks | Recovery tests logged; RPO/RTO defined | |
| Automated deployments & updates | Closes known vulnerabilities quickly; reduces manual errors | Rollout process documented; update status visible for edge/brokers/hubs | |
| Network & communication | No open inbound ports in OT segments | Minimizes direct attack surfaces | Firewall rules checked; external port scans without hits |
| Edge only connects outbound (e.g. MQTT) | Prevents inbound connections to critical networks | Edge configuration documented; connection direction technically enforced | |
| Broker as central OT/IT hub (publish/subscribe) | Decouples producers/consumers; reduces lateral movements | Architecture diagram; proof of function Pub/Sub paths | |
| Outbound ports limited to a minimum | Controls data flows and exfiltration | Firewall allowlists; regular port reviews | |
| Protocol security | Conversion of insecure OT protocols to MQTTS | Prevents plaintext sniffing and tampering | Edge maps/flows documented; test recordings show TLS |
| Broker only accepts MQTTS | Forces encryption in the UNS | Broker-Config (TLS-only); connection attempt without TLS is rejected | |
| X.509-Mutual-Auth for Edge/Broker/Clients | Strong, two-sided identity verification | Certificate CA stored; expiry monitoring & revocation lists available | |
| Auth & Access | Least privilege principle implemented | Reduces the risk of misuse and operating errors | Roles/rights matrix; regular recertifications |
| ACLs for MQTT topics defined and checked | Fine-grained control of publish/subscribe | ACL rules versioned; test cases for allowed/forbidden topics | |
| Username/password authentication hardened | Prevents trivial compromise | Complexity rules, rotations, no default credentials | |
| Integration with corporate identity providers | Central identities & policies, less duplicate administration | Connection to e.g. Microsoft Entra/LDAP/Kerberos; SSO where possible | |
| Session and activity monitoring on the broker | Detects anomalies and unauthorized operations | Session logs; alerting in the event of policy violations |
Conclusion
The Unified Namespace (UNS) is a cornerstone of modern Industry 4.0 architectures, but as a critical data hub it requires robust protection. Risks can only be minimized through consistent implementation of network segmentation, encrypted communication, strict access controls, and centralized governance. Outbound-oriented protocols such as MQTT and the conversion of insecure OT protocols into MQTTS play a key role in securing IT/OT connectivity. Organizations that adopt these best practices early build not only a secure but also a sustainable and future-ready UNS architecture.