In the Industrial IoT, the Unified Namespace (UNS) architecture has emerged as a strategic foundation for efficient, scalable data management. To fulfill this role effectively, the UNS must be built on a well-structured architectural design. Each functional building block of the UNS must meet specific requirements of modern production environments – such as scalability, edge readiness, redundancy, security, and monitoring. To get a structured overview, the following sections outline the key components of an industrial UNS architecture, along with typical requirements in the context of Industry 4.0.
The Unified Namespace (UNS) as a Single-Source-of-Truth
The Unified Namespace (UNS) is an architectural principle for the central organization of industrial data streams. It defines a common data space where information from OT and IT systems is standardized, contextualized, and made available in real time—regardless of source, format, or location. Acting as the factory’s single source of truth, the UNS ensures that all systems—from machines to cloud platforms—access the same consistent data, eliminating redundancy, inconsistencies, and data silos.
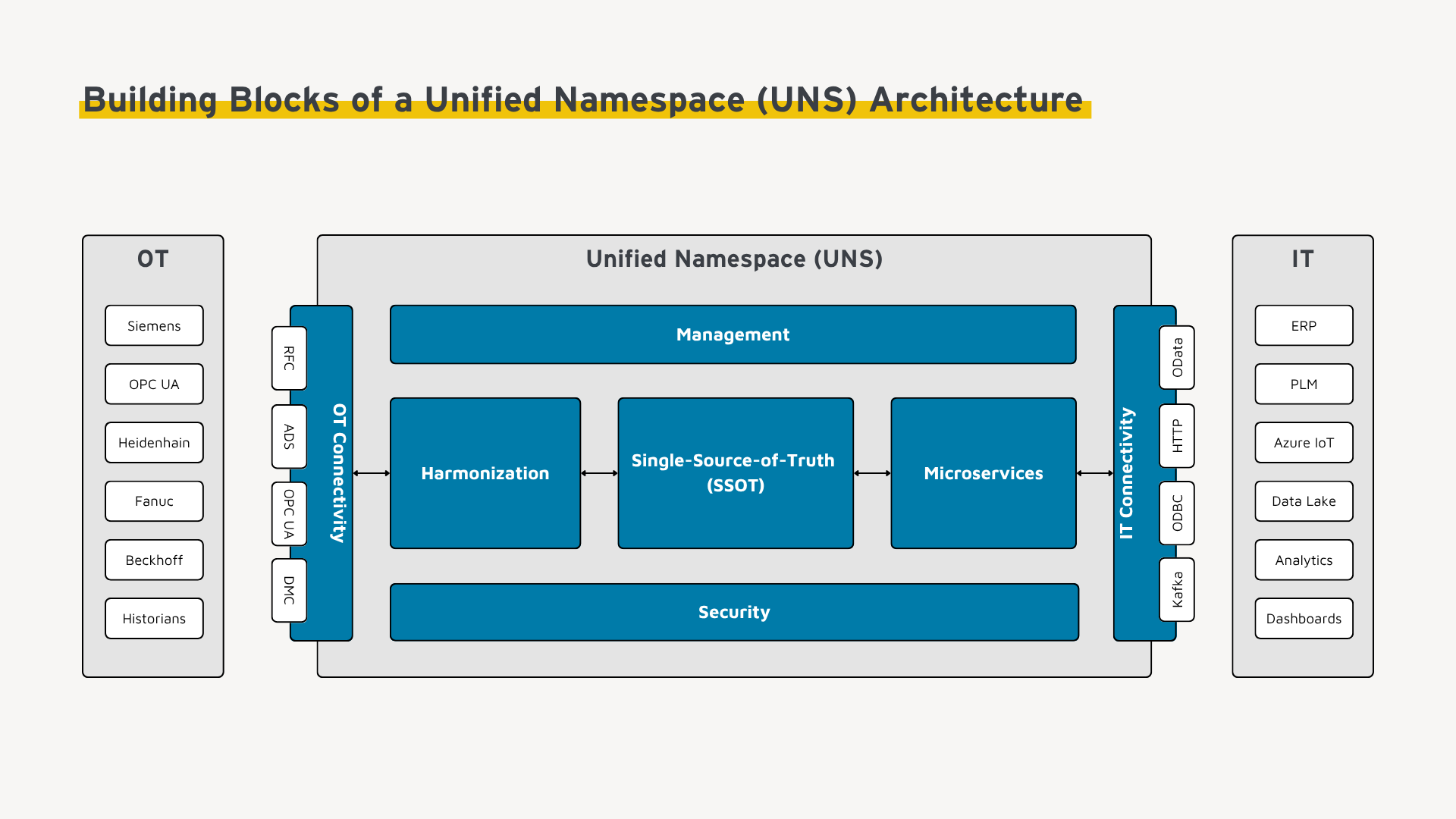
Building Blocks of the Unified Namespace (UNS) Architecture
A Unified Namespace (UNS) is based on 6 functional building blocks that together create a scalable, resilient and semantically consistent data architecture for industrial applications. The following sections outline these key components.
1. IT/OT Connectivity: Gateway to the Single-Source-of-Truth
The connectivity layer is a foundational element of any Unified Namespace (UNS) architecture. It serves as a universal translator between diverse OT and IT systems — machines, sensors, PLCs, and enterprise applications — and the Single Source of Truth (SSOT). Given the wide variety of systems in industrial environments, each using different protocols (e.g., OPC UA, Siemens S7, Modbus, SAP RFC), the connectivity layer ensures seamless, reliable, and standardized integration into the UNS. This eliminates protocol fragmentation and establishes the foundation for consistent data flow across the enterprise.
2. Harmonization —The Key to Scalability
The harmonization layer is the backbone of a scalable Unified Namespace (UNS) architecture. In industrial environments, machines, controllers, and sensors output data in proprietary formats with inconsistent structures, identifiers, and units. Without centralized semantic harmonization, this heterogeneity leads to fragmentation and complexity within the Single Source of Truth (SSOT), often requiring time-consuming point-to-point mappings.
3. Single-Source-of-Truth (SSOT) for Factory Data
At the core of any Unified Namespace (UNS) architecture lies a dependable data layer that serves as the Single Source of Truth (SSOT). It guarantees that both OT and IT systems access consistent, unified, and context-rich data. Depending on the use case, the SSOT can take on various technical forms, each suited to different requirements. Common implementations include:
- Message brokers for high-frequency, event-driven communication using protocols such as MQTT, NATS, or Kafka. Organizations may use a combination of these to meet both performance and integration needs across complex OT/IT landscapes.
- MQTT excels at connecting massive fleets with thousands to millions of IoT devices due to its lightweight protocol design.
- Kafka provides a robust, scalable backbone for real-time data streaming and analytics of large data volumes within IT environments.
- NATS combines low latency with high performance and is suitable for hybrid scenarios.
- Relational databases (e.g. SQL) for structured, transactional data.
4. Microservices – Distributed Logic in the Unified Namespace (UNS)
Microservices represent the scalable processing layer within a UNS architecture. Each microservice encapsulates a specific piece of business logic — such as OEE calculation or data enrichment — in a modular, self-contained functional unit. These services can be deployed, updated, and scaled independently, allowing new functionalities to be introduced without disrupting the overall system. This architectural flexibility enables agile development and fosters cross-functional collaboration: for example, production teams can build services for condition monitoring, while quality teams focus on analytics or traceability. All teams work against the same consistent data foundation provided by the UNS. Typical examples of microservices include:
- OEE (Overall Equipment Effectiveness) calculation
- Data enrichment using master or process data
- Confirmations and material updates to ERP systems
- Condition monitoring for machines and systems
- Anomaly detection based on real-time data
- Traceability services for tracing material and process data
- Quality analyses, e.g. on the basis of measurement data or reject rates
- Energy monitoring for recording and evaluating energy consumption data
5. Management: UNS Monitoring, Deployment and Governance
The management layer serves as the orchestration backbone of a Unified Namespace (UNS) architecture. It centralizes key capabilities for deployment, configuration, monitoring, and governance — spanning from the edge to the cloud. This layer ensures that all operational components, including connectors, brokers, and microservices, can be efficiently managed and coordinated across distributed environments. Core responsibilities of the management layer include:
- Central management of decentralized edge and broker instances
- One-click deployment and updates of configuration packages
- Configuration of central and local redundancy and failover mechanisms
- System health monitoring via metrics, logs and alerts (e.g. through Prometheus)
- Enforcement of security and access policies (RBAC, certificate management)
- Integration into CI/CD processes
- Central template management and instantiation for recurring configurations (e.g. harmonizations, microservices)
- Management and versioning of configurations (e.g. semantic models, microservices)
By providing a unified control plane, the management layer becomes the central access point into the UNS ecosystem. Without it, consistent governance, efficient scaling, and cross-site orchestration of UNS deployments would not be possible.
6. Security – Building Trust in the Unified Namespace (UNS)
Security is a foundational requirement for operating a Unified Namespace (UNS) in industrial environments, where data availability, integrity, and confidentiality are critical. As a cross-cutting concern, security must be embedded throughout the architecture — following a “security by design” approach. Since the UNS spans from edge devices to the cloud and processes sensitive production data across heterogeneous systems, robust protection mechanisms are essential at every level. Key security capabilities include:
- End-to-end encryption via TLS for protocols such as MQTT, HTTP, and OPC UA
- Authentication & authorization using X.509 certificates, API keys or OAuth2
- Fine-grained access control (Role-Based Access Control, RBAC)
- Support for a segmented network infrastructure to separate OT and IT networks
- Audit logging for audit-proof traceability and compliance
- Central certificate management across all UNS components
To be effective at scale, the security architecture must be centrally configurable and consistently deployable across sites — ideally integrated into the management layer. This enables a unified, secure data space that aligns with industry standards and regulatory frameworks such as ISO 27001 or NIS2.
Requirements for UNS Building Blocks
In industrial environments, each UNS building block must fulfill specific technical and operational requirements depending on the use case. The following overview outlines key requirements — from connectivity and data harmonization to governance, scalability, and security.
Building Block Specific Requirements
| Function | Requirement | Description |
|---|---|---|
| 1. Connectivity | Broad protocol support | Supports a wide range of OT/IT protocols such as OPC UA, HTTP or PLC protocols. |
| SDK for expandability | Custom extensions can be developed independently of the vendor. | |
| Polling and event-based | Depending on the source system, either polling or event-triggered communication is supported. | |
| Closed-Loop | Allows direct communication between machines for synchronization or reaction. | |
| 2. Harmonization | Data standardization & semantics | Standardizes proprietary data formats into standardized information models according to common industry standards such as OPC UA Companions or ISA-95. |
| Local data processing | Contextualizes, aggregates and enriches machine and process data close to the source. | |
| Data buffering & offline capability | Buffers data locally on the edge in the event of a connection failure to the central UNS and forwards it later without loss. | |
| 3. Single-Source-of-Truth (SSOT) | Real-time and batch data | Processes both high-frequency machine telemetry and batch information (e.g. order data). |
| Distributability and synchronization | Supports distributed SSOT instances (e.g. per line, plant or region) and automatic synchronization for consistency across locations. | |
| Scalability on edge & cloud | SSOTs are horizontally scalable through clustering in order to cope with high throughput rates (cloud). They also support topological distribution – e.g. dedicated brokers per machine or line – for scaling on the edge. | |
| 4. Microservices | Independence and encapsulation | Each microservice can be provided, updated and scaled independently of other services. |
| Domain orientation | Teams develop microservices specifically along functional domains – for example for machine availability, material tracking or quality inspection. This simplifies maintenance and strengthens functional responsibility. | |
| Edge and cloud capability | Microservices can run at all levels – locally on edge devices for latency-critical use cases or centrally in the cloud for data-intensive analyses. | |
| 5. Management | Governance | Centrally managed via a unified interface or API, components remain locally autonomous. Site-wide rollouts and configurations are one-click operations. |
| Monitoring and logging | All components provide telemetry data, metrics and logs to monitor the overall system. | |
| Central security configuration | It must be possible to configure the security architecture centrally and roll it out consistently across all locations. | |
| 6. Security | Security-by-Design | Integrates advanced security mechanisms such as TLS encryption, RBAC, network segmentation and audit logging. |
| Certificate management | Enables centralized management and renewal of TLS certificates across all system components. | |
| Access control | Supports fine-grained user and role management for data and services – ideally integrated with central identity services such as Azure Entra ID. |
System-Wide Requirements
| Requirement | Description |
|---|---|
| Decoupling of systems | Systems are loosely connected via standardized interfaces such as MQTT or NATS. The UNS serves as a buffer and integration layer to enable system integration without dependencies. |
| Modularity | The UNS consists of specialized components. These can be scaled, deployed and developed independently. |
| Single source of truth | All OT and IT systems access a consistent database to avoid redundant and contradictory information. |
| Edge-to-cloud capability | UNS components are containerized and can be operated in a lightweight manner on edge devices or in the cloud. This supports a unified, consistent deployment model across all environments. |
| Scalability | Brokers, microservices and connectors are horizontally scalable (e.g. through clustering or topological separation per line or machine). |
| Redundancy | The UNS must absorb failures of individual components – through clusters, local redundancy on the edge, fallback buffers and automatic re-synchronization. |
| Event-based & cyclic polling | The architecture is optimized for event-based communication in order to minimize latency and resource consumption. However, pull-based mechanisms (polling) are supported (e.g. for PLC communication) as well. |
| Support for real-time and batch data | The architecture must reliably ingest, process, and deliver both high-frequency real-time data and batch information. |
| Low-code capability | Scaling a UNS is not an achievement of a few developers – it can only be achieved across departments. The components therefore support low-code in order to integrate central IT and decentralized OT teams. |
| Performance and latency | The system architecture is optimized for minimal latency at thousands of data points per second in order to support local time-critical applications such as alerts or control commands. |
| Delivery guarantees | The architecture offers delivery guarantees for messages – for example through QoS levels. |
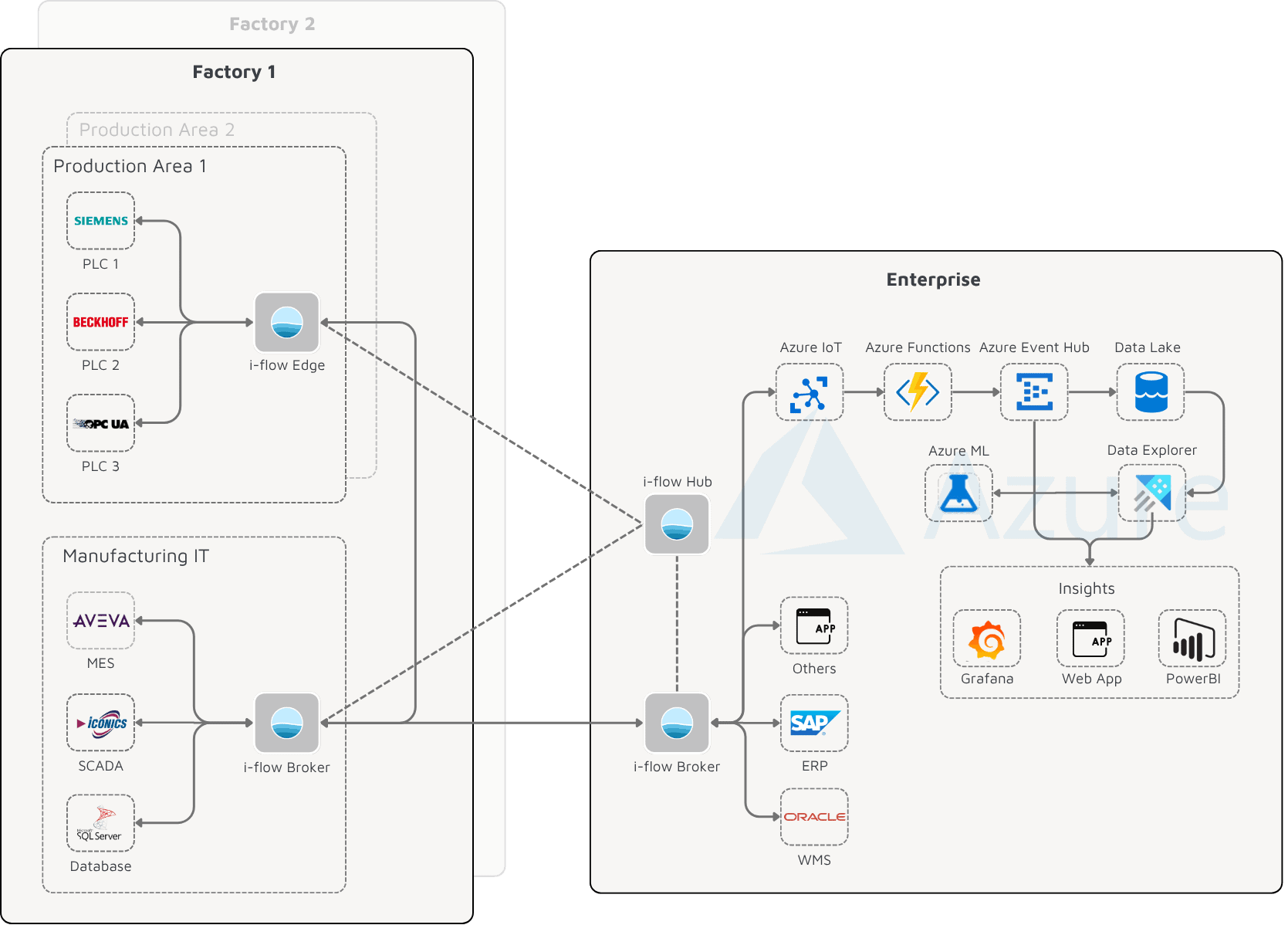
Unified Namespace (UNS) Reference Architecture
The implementation of a Unified Namespace (UNS) requires a coherent, component-based architecture design. A tried and tested structure follows the principle of functional separation as described in this article: connectivity, harmonization, single source of truth (SSOT), microservices, management and security are clearly delineated, coordinated functions. In a typical architecture design, these building blocks are implemented along three infrastructure layers: Edge, Message Layer and Central Management. The following architecture diagram shows a real-world implementation.
The building blocks are directly reflected in these components:
- i-flow Edge for the local integration and harmonization of heterogeneous OT and IT systems – for example via OPC UA, Modbus or manufacturer-specific protocols.
- i-flow Broker as SSOT, ensures consistent data distribution along a defined UNS namespace
- i-flow Hub as a management platform enables cross-site deployment, monitoring and governance of all edge and broker instances.
This architecture adheres to proven UNS principles — modularity, decoupling, scalability, and hybrid edge-to-cloud capability — and integrates into existing IIoT landscapes. Local nodes operate autonomously while automatically synchronizing with central systems, resulting in a robust and consistent infrastructure from sensor to cloud. A real-world application example of this architecture can be found here.
Conclusion
A powerful Unified Namespace (UNS) architecture is far more than just a message broker — it is a strategic framework for holistic, scalable, and semantically consistent integration of industrial data. At its core lies the Single Source of Truth (SSOT), supported by dedicated layers for connectivity, harmonization, and processing. This functional decoupling enables the design of IIoT landscapes that are flexible, robust, and multi-tenant — from edge to cloud. Organizations that build their UNS on clearly defined architectural principles lay the foundation for end-to-end transparency, accelerated innovation, and a future-ready smart factory.